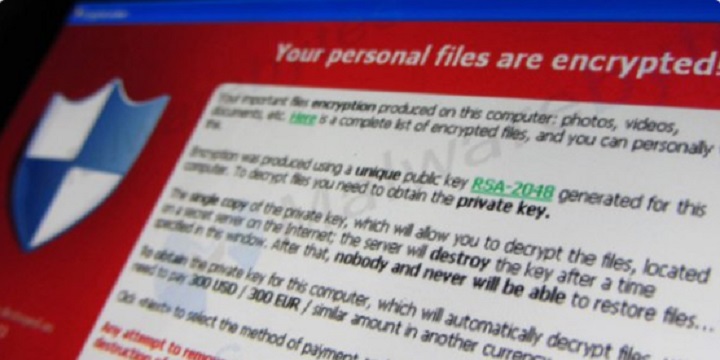
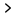Companies around the world are putting extra attention on their cyber security as reports of several European-based firms being struck by a ransomware attack. The attack is identified as a virus that freezes computers, seizing the user’s access to their files, with a demand for an untraceable ransom to be paid through Bitcoin to a provided address.
Ukraine seems to be the most affected by the attack. Several Ukrainian companies, including the national power company Ukrenergo (traded privately) and the main airport of Ukraine’s capital, Kiev, were amongst the first affected by the attack. The Chernobyl nuclear power plant was also affected — after shutting down the Windows-based sensors at the plant, radiation levels had to be checked manually. Additionally, the Kiev metro system has halted payment cards, several petrol stations have stopped operations, and Ukraine’s government systems have been affected.
Other companies such as WPP (LON:$WPP) (NASDAQ:$WPP), a British advertising agency, have also suffered the consequences of the attack, mainly disruptions to the IT systems. Problems that have arisen due to the attack have also affected Ukrainian aircraft manufacturing company Antonov (traded privately), Russian oil company Rosneft (MCX:$ROSN), Danish shipping company Maersk (CPH:$MAERSK-B), Netherlands-based shipping company TNT (acquired by FedEx (NYSE:$FDX)), French construction company St. Gobain (EPA:$SGO), U.S. pharmaceutical company Merck Sharp & Dohme (NYSE:$MRK), U.S. law firm DLA Piper (traded privately), U.S. hospital operator Heritage Valley Health System (traded privately), food company Mondelez International (NASDAQ:$MDLZ), a Cadbury (NYSE:$CBY) factory based in Australia, and two postal services based in Ukraine. Some of these companies have yet to confirm the attack, while others have shut down their systems or halted operations as a precaution.
Government Involvement
According to the U.S. National Security Council, multiple government agencies are investigating the attack. International police cooperation Interpol has said that it is keeping track of the conditions of the attacks, collaborating with its member countries in order to pinpoint who is responsible.
The U.S. Department of Homeland Security has advised those who have been affected to not pay the ransom, as there was little to no guarantee that access to files would be granted if the instructions were followed. Despite the warnings of Homeland Security, however, a bitcoin wallet associated with the attack has already received several payments totaling to about 3.5 bitcoins, or $8,670.
Russian cyber-security company Kaspersky Lab (traded privately) have analyzed the attack, saying there have been about 2,000 systems affected — mainly in Ukraine, Russia, and Poland. It is also suspected that other countries like Italy, Germany, France, the UK, and the US have also been affected as well.
The Ransomware
Some experts believe that the current attack makes use of the security weaknesses caused by the WannaCry attack that had occurred in May. Chris Wysopal from Veracode (traded privately) said that WannaCry had exploited several Windows code loopholes during its attack, which the current attack is now making use of. Many companies that had been affected by WannaCry did not patch these holes correctly as the attack was dismantled very quickly, Wysopal explained. Other companies that have been affected also have a record of struggling with patching software quickly and efficiently. “These organizations typically have a challenge patching all of their machines because so many systems cannot have downtime,” Wysopal said, “Airports also have this challenge.”
Systems that rely on anti-virus instead of being patched are defenseless, Wysopal noted after copies of the virus were sent out to check if security software like anti-virus systems could catch the virus and stop it. Only two vendors were able to spot the virus, Wysopal said.
At first, the current attack seemed like it used the ransomware in the WannaCry attack, said computer science professor Alan Woodward. The WannaCry attack made use of a ransomware called Petya as well as the updated version of Petrwrap. But it’s not so clear now if this is true, Woodward noted.
Kaspersky Lab believes that the ransomware used in this attack is one that hasn’t been seen before, despite being similar to Petya. The company has now taken to calling the ransomware NotPetya as a result.
More on Cyber Attacks
A spokesperson for Recorded Future (traded privately) — a US-based cyber-security company — Andrei Barysevich, said to the BBC that it is unlikely that the chances of these kinds of cyber-ware attacks will lower in the future because they are very profitable for cyber-thieves.
As an example, Barysevich noted a South Korean company, Nayana, that was affected by the WannaCry attack. The company paid $1 million to get their data back, Barysevich said. That kind of money is the biggest motivation for any cyber-thief out there.
Featured Image: Twitter